Let's Play With Consul
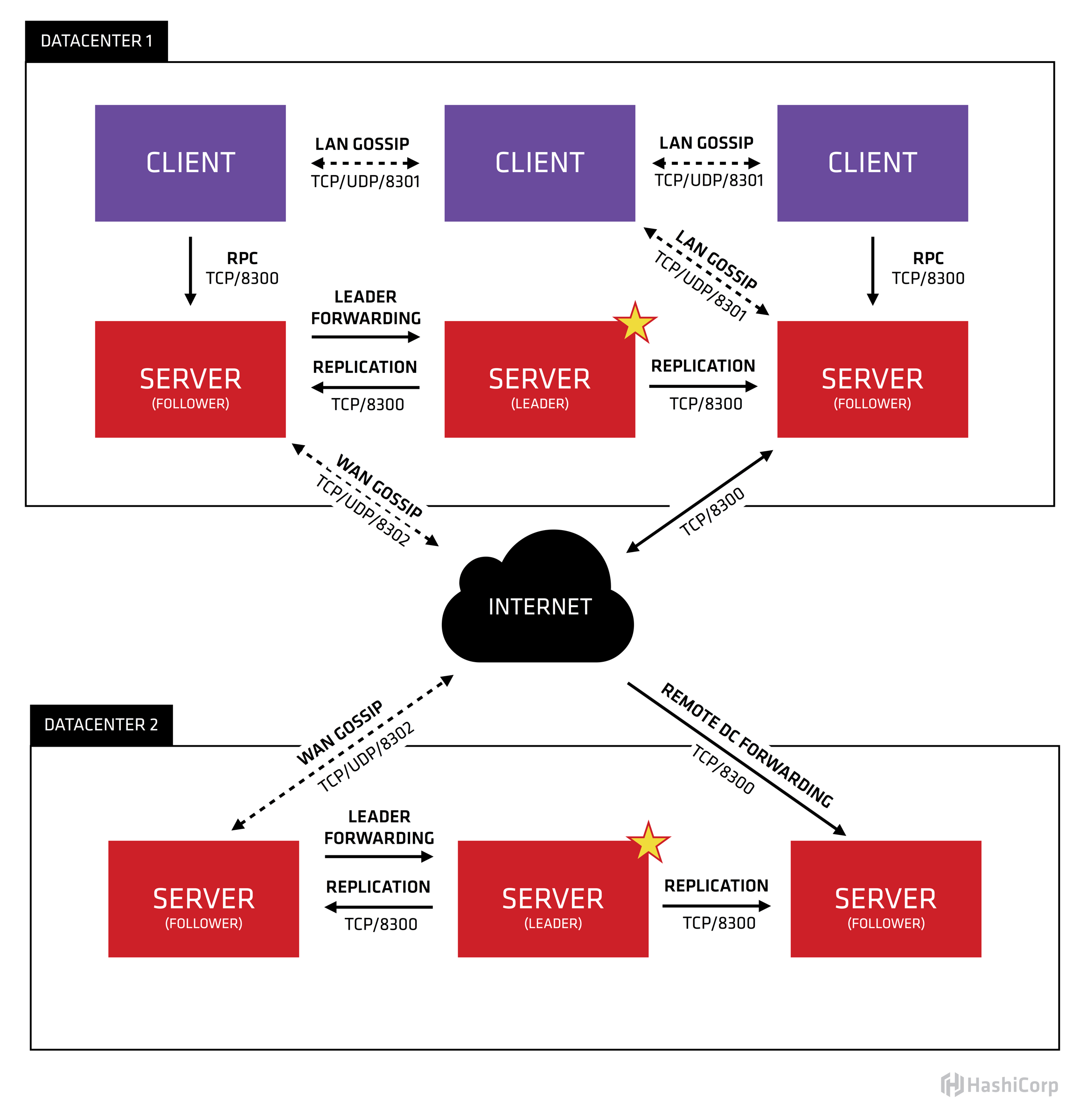
Consul consists of a fairly simple Server-Client architecture, where users of Consul talk to Consul Clients, and Consul Clients talk to Consul Servers, and Consul Servers talk to one another.
Download Consul Locally
info
This script requires unzip to be installed, and sha256sum isn't necessarily the same across OS distributions.
This script has only been tested on Ubuntu Linux 18.04 and Amazon Linux 2.
They have an official deployment guide that's pretty great, and a security guide that's not half bad as well.
Create Certificates
Consul CLI now a tls command for quickly building certificates.
For this workshop if you go to the examples/consul-cert folder we'll be able to make all of this work with provided server configurations.
Create the Consul CA Certificate
Create the Consul Server Certificate
Create the Consul Client Certificate
This will create Client certificates in pem format:
This will create a pfx certificate bundle which can be imported into our browser:
It's recommended to supply a password, because sometimes software will prevent the import of bundles with no passwords.
Validate Local Server using TLS
Consul CA Certificate
Let's use openssl to read the certificate:
We see a few interesting things:
Hashicorp actually fills in slightly more valid Issuer and Subject attributes.
And our certificate is a CA.
Consul Server Certificate
We'll see the Subject Common Name contains the server.dc1.consul name which is required per Consul's own
security mechanisms to ensure that this node can be a Server in the cluster:
And we'll see that this certificate is good for both Web Server and Web Client authentication:
This is because the Consul Server is both a Server when it serves requests, and a Client when it connects to other Servers to transfer state back and forth.
Finally, we some Subject Alternative Name values that allow us to make connections locally to the server:
Consul Client Certificate
We'll that this is a Consul Client based on it's Common Name:
However, this certificate can still be used as a Server and Client certificate:
and this is so that processes on the local machine can talk to the local agent over SSL. Remember, for Consul, it's the Common Name
that determines if the certificate is for an agent running in Server or Client mode.
Look at the Private Keys
Install the consul-agent-ca.pem so we trust it.
Every application is a bit different. It's a bit maddening.
To install the CA on a linux host you might do the following:
If you're using Firefox and Chrome you'll need to import the Certificate. On Linux these applications have their own keystore solutions. On macOS Chrome still uses the Apple Keychain.
warning
On macOS, importing the certificate into Apple Keychain isn't enough. You also need to open the certificate and tell the OS to trust the certificate for whatever purposes you believe it should be trusted.
There's also a certutil tool that can help automate some of this.
Finally, you need to also import the consul.pfx file into your browser or Apple Keychain. This will allow you to do
two-way, or client side SSL. What this means is that your client will also present a certificate to the server to validate
your authenticity.
Run a Local Server Using Our Certificates
Start the Consul server:
Open a browser to https://localhost:8501
This time the server will request a client certificate, and it will use the one we imported previously.
curl can work with certificates too: